Despite its enormous scale, Amazon Web Services (AWS) continues to grow rapidly. In the fourth quarter of 2021, revenues surged by 40% to $17.8 billion, and the operating income came to more than $5 billion.
But as the cloud becomes more pervasive, it may be tougher to keep up the growth.
“More and more of those workloads will live in the cloud, but that will take time, and inevitably, some of them will probably never move over,” said AWS CEO Adam Selipsky at last year’s VMworld conference.
The reality of increasingly demanding regulations, especially in financial services in healthcare, is proving to be an obstacle for cloud growth.
According to Gartner, about 65% of the world’s population will have their data covered by privacy regulations. This is up from 10% in 2020. In light of this, it should be no surprise that enterprises still see on-premises environments as a good option.
“The last great barrier to migrating IT to the cloud is addressing the understandable fears of the chief information security officer (CISO) regarding data security,” said Ayal Yogev, CEO and co-founder of Anjuna Security. “There’s good reason to be concerned; workloads and data executed and stored in the public cloud expose data to too many people—good and bad.”
Yet, there are emerging innovations in security to make it more palatable to migrate sensitive workloads to the cloud. One of them is confidential computing, which provides security at the chip level. It has been showing lots of traction during the past few years.
Also read: 5 Emerging Cloud Computing Trends for 2022
What is Confidential Computing?
Simply put, data has three states. It can be at rest, in use, or in transit.
It’s true that data can be encrypted while it is in the first two states, yet there are still vulnerabilities when it is in use or being processed. The reason is that before the application can be executed, the data is temporarily unencrypted, allowing just enough time for an intrusion.
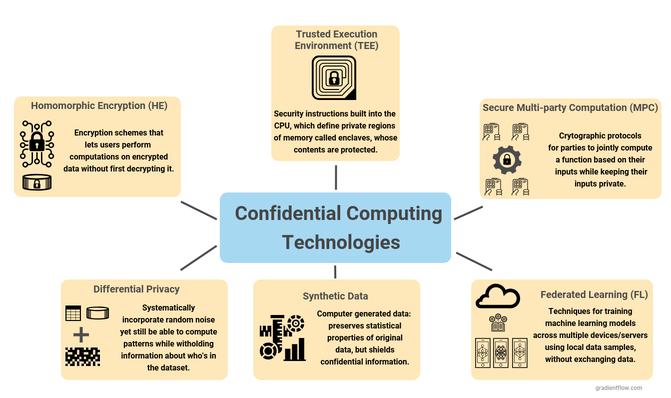
To secure this data, there needs to be another layer of protection, which is embedded in the central processing unit (CPU). This is called a trusted execution environment (TEE), or enclave, which uses embedded encryption keys. The result is that the data remains protected while in memory.
“Memory and other resources will be protected by cryptographic keys that prevent unauthorized access to the data,” said Ben Richardson, senior software engineer at SecureW2. “Encrypting data in memory means it can’t be read by software that isn’t authorized to do so … even if the unauthorized software is running on the same physical server as the data.”
In 2016, Intel launched the first confidential computing system with its SGX platform. Since then, many other large vendors have adopted the technology, including IBM, Amazon, Advanced Micro Devices, Alibaba, Google, and Nvidia.
Also read: The ABCs of Smart Cloud Migration
Why Confidential Computing is Important
While working with third-party cloud providers can result in lower costs, there is the issue of trust and knowing whether the company is doing enough with security.
But with confidential computing, there is a zero-trust security. That is, the cloud provider does not have access to the data because there is no time when it lacks encryption. This certainly provides for confidence in moving workloads to the cloud.
“Confidential computing is ushering in a new era to enable analytics of sensitive data without violating privacy and confidentiality requirements,” said Baffle CEO Ameesh Divatia. “It will address a significant roadblock for enterprises wishing to migrate to the cloud because it prevents cloud administrators from being able to view their customers’ data.”
A report from Gartner predicts that by 2025 about 65% of large organizations will use one or more privacy-enhancing computations approaches. The report highlights that confidential computing will be one of the most important.
The Challenges and Future of Confidential Computing
Even though confidential computing has much promise, there are still some lingering issues.For example, it can require substantial processing compute to enable it.
“Cloud providers are creating a dedicated infrastructure that supports confidential computing, but this approach creates a hardware dependency that may restrict customers’ ability to run across disparate cloud providers or pursue a multicloud strategy,” said Divatia.“Existing application and database environments will need to be redesigned to work with confidential computing; although, there is scope for innovation to minimize the operational burden.”
Another problem is that it can be complicated to set up and manage. The fact is you need a team with deep technological skills.
Yet, startups are already beginning to address this issue. And given the importance of cloud migration, there will likely be more investment in confidential computing. It definitely helps that there has already been adoption from large chip manufacturers.
“With the rise of data consolidation in the cloud and the accompanying need for secure data sharing, organizations will need to protect their sensitive data in the cloud with new computation models that incorporate privacy-preserving analytics and innovative architectural models,” said Divatia.
Read next: Cloud Security Best Practices for 2022




