Introduction
Falcon Horizon, CrowdStrike’s Cloud Security Posture Management solution, uses configuration and behavioral policies to monitor public cloud deployments, proactively identify issues and resolve potential security problems. However, customers are not limited to predefined policies. This article will review the different options for creating custom cloud security posture management policies in Falcon Horizon.
Video
Policy Configuration
The main Falcon Horizon dashboard illustrates an overview of recent findings across all registered cloud accounts and providers.
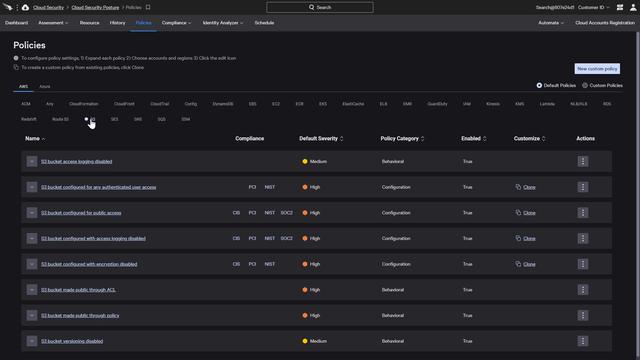
Those findings are based on the policy configuration. The “Policies” tab displays comprehensive options, categorized by provider and service, to monitor for cloud misconfigurations as well as malicious behaviors. In this example for Amazon’s S3 service, there are a number of policy options for both categories. Falcon Horizon also provides the functionality to create custom policies tuned to best meet the needs of an organization.
Creating a Custom Policy
From the “Policies” tab under “Cloud Security Posture”, there is an option to create a “New custom policy”.
A wizard will guide the creation of the new policy. The first step is to choose the applicable cloud provider.
Next, a new policy name, description and severity are assigned. In the example below, this custom Azure Identity policy is a medium severity.
To create a new policy from scratch, the next step is to choose an asset type that will correspond to the cloud service. The example below shows an asset type of AD user. (The option to select a baseline policy will be covered under “Modify Existing Policies”.)
Once the asset type is selected, filters and conditions can be added. Adding rules based on any number of additional criteria including specific accounts, groups, or tenants make the new policy more specific. Shown below is a policy that looks for enabled accounts where the credentials that are not registered for MFA, but the credential itself is enabled.
Modify Existing Policies
In many situations, it can be useful to start with an existing rule and make changes or additions. There are two different ways to approach that in the user interface. From the policies list, some policies include a “Clone” link. Cloning a policy will carry over all of the policy and compliance details, while allowing changes to the rule criteria.
Alternatively, selecting the “New custom policy” option will present options for the applicable cloud provider.
Next, there are prompts to enter a custom policy name and severity before selecting the appropriate cloud service. The following screen includes two main options. As shown above, selecting an asset type is the first step to creating a blank policy. In contrast, choosing to start with an existing baseline policy will replicate that policy and the associated query logic (shown below for AWS EC2).
Once the cloned or baseline policy has been selected, there are a number of options to make changes. The existing fields and operations can be edited. While the trash can icon provides the option to delete criteria, new criteria can also be added using any number of fields. In the example below, ports considered high risk can be added or deleted. A rule for tag name has been added to ensure that this rule will be triggered any timepublic ingress on high risk ports is allowed to systems with a tag NOT equal to “test”.
The highlighted “Test custom rule” option above provides a preview into how that rule will perform in the environment.
Compliance
After saving the custom policy filters, there are options to map that policy to compliance controls. While cloned policies will already include any compliance associations, those can also be modified as needed.
When using a policy baseline or starting from scratch, the next step will present menu options for compliance. The CrowdStrike integrated compliance frameworks can be selected, but there is also the option to “Add new compliance”.
By populating just a few fields, policies can be associated to a custom benchmark or compliance frameworks that are currently not incorporated into the platform.
Once the requirement has been saved, it will appear in the drop down so that the version, section and requirement can be mapped with the custom policy before saving.
After mapping compliance, the next step is to save the policy.
Assessments
New policies will be listed under the “Policies” tab as custom policies. The buttons at the top pivot the display between default and custom policies for each service.
With the default and custom policies in place, assessments are performed on regular, configurable intervals. The assessment findings can be filtered to quickly concentrate on a specific severity, account, region, service or type. Also, a “custom” flag is used next to the policy name to help identify those tailored policies.
Conclusion
As organizations continue to deploy mission critical data and applications to the cloud, it is critical that those resources are properly configured and protected. In addition to monitoring multi-cloud deployments for misconfigurations and behaviors, Falcon Horizon enables customers to build custom policies that best meet their organizational and compliance needs.
More resources




