Ah, the eternal question: Should you protect your iOS device with a passcode? On one hand, the knowledge that your data is presumably safe from prying eyes makes carrying around your phone and tablet less worrying; on the other, having to tap in a code every time you want to check your email or make a phone call can quickly become annoying.
Apple, for its part, isn’t helping make this choice easier for consumers: Methods for
bypassing
the passcode screen or
circumventing it altogether
keep getting discovered, and though the company typically provides patches fairly quickly, these security holes don’t instill confidence in iOS’s ability to keep our data safe.
Besides, passcodes seem inflexible and at times even incompatible with the way we use our devices. I’ve stopped counting the number of people who have asked me why iOS doesn’t use geolocation to automatically engage passcodes when, for example, you leave your house, where you don’t need so much protection. And when you leave your passcode-locked device within reach of a toddler, you can find out rather quickly that Apple’s deterrents aren’t exactly designed with curious children in mind.
A look behind the scenes
On the surface, therefore, passcodes act as little more than gatekeepers to your devices—and, therefore, to the data stored on them. Like a watchful security guard, iOS becomes increasingly suspicious when incorrect codes are tapped in, and it requires longer and longer pauses between attempts until, after it counts ten tries, it either locks the device up for good or—depending on your settings—wipes out the data altogether.
If an iOS device’s security consisted of nothing more than a passcode, however, then the system would be ineffective. It’s relatively easy for a skilled hacker to bypass this locking mechanism by downloading the contents of your device’s flash memory and, thanks to software tools ready-made for this very purpose,
gaining access to its every byte in a matter of seconds.
Therefore, Apple, a
ware that its mobile device would likely be taken to (and lost in) all sorts of public places, baked security right into its hardware, creating a subtle interplay of technologies in which passcodes play a small but crucial role.
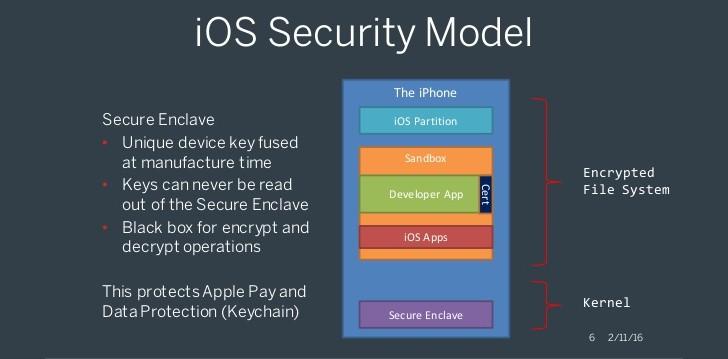
Encryption for all
iOS security begins during manufacturing, when a unique encryption code is baked right into every device.
iPad and iPhone security begins at the factory, where two special codes are burned right into the hardware; the first is a code that’s unique to each device, while the second code changes from product line to product line. Thus, for example, each iPhone 5 will have its own unique code, plus a code that identifies it as an iPhone 5.
iOS uses these codes, together with a bit of random data called
entropy
, to generate a master cryptographic key, which is then stored in a dedicated area of memory called
effaceable storage
. Even though the hardware codes never change, the entropy ensures that this process, which occurs every time you restore your device, results in a different key every time.
Subsequently, every file that is created on the device is encrypted with a separate key derived in part from the master; because iOS devices support encryption directly in the hardware, this process is typically fast and transparent to the user, and results in files that are unintelligible without the master key.
Should you ever need to completely wipe out a device—say, because it’s been stolen, because you’re selling it to someone else, or just because you’re reinstalling iOS—all that the operating system needs to do is erase the effaceable storage, and voilà
:
All the data stored on the device’s disk becomes unusable, even though it’s technically still there. When you install a new copy of the operating system, a new master key is generated, and the process starts over again.
This storage-based approach is important for two reasons: First, it’s relatively quick and efficient—that can save time at a critical juncture if, for example, there’s only a small window of opportunity to erase the device’s contents when a thief turns it on to see if it works. Second, it helps to extend the life of the device’s flash memory, which can only be written to so many times before it starts to fail.
Enter the passcode
Useful though this security scheme may be when a quick wipe is called for, it does
not
protect your data from prying eyes, because the key used to decrypt the data is stored right on the device, where a skilled hacker could easily retrieve it.
This is where the passcode comes into play: When you turn the passcode lock on, a technology called Data Protection kicks in, causing a new encryption key to be generated; it’s used
to encode certain files that have been marked as critically important by the operating system—like your Keychain—as well as by individual apps.
Crucially, the passcode itself is used as part of the encryption key, and then discarded when the device later locks. This way, iOS becomes physically unable to decrypt the data until the user re-inputs the passcode.
Because the passcode is not stored anywhere on the device, the only way to decrypt the data without it is to use a brute-force approach: that is,
to try all the possible codes until you find the right one.Four-digit passcodes are easy to remember … and easy to break.
The fact that the passcode isn’t stored on your device is, incidentally, the reason why Apple can’t help you if you’ve lost your passcode, and why iOS can’t automatically turn off passcodes when you’re inside your home: The unlocking code you pick is physically required to encrypt the data, and it is never stored on the device. Any arrangement to the contrary, even in the name of convenience, would introduce a massive security vulnerability and effectively undo any advantage such encryption offers in the first place.
The weak link
Unfortunately, passcodes’ dependence on human intervention makes them the weakest link in the iOS protection scheme. People are notoriously bad at choosing security over convenience, and many of us unwittingly weaken the safety of our data through poor “security hygiene” practices.
For example, iOS defaults to requiring four-digit passcodes, which most people pick because they are easier to enter single-handedly on the large numeric keypad. According to
Apple’s own security whitepaper
, a malicious attacker who gains access to a device’s contents could defeat a four-digit passcode in a little over a minute, using nothing more sophisticated than a simple program that tries all 10,000 possible combinations.
But it gets worse—
research has shown
that many people choose extremely weak passcodes like “0000” and “1234,” giving would-be hackers an easy means of attack. In fact, there’s a better than one-in-five chance of that they can gain access to your phone with just five attempts, simply by guessing the most common choices.
Picking better passcodes
It’s possible to use the numeric keypad with passcodes longer than four digits—as long as they are made up entirely of digits.
Fortunately, it doesn’t take much effort to dramatically increase the security of your passcodes. For starters, if you like numeric codes because they’re easy to input using the on-screen keypad, you’ll be happy to know that iOS uses the same entry mechanism even if you pick a code longer than four digits. To enable it, open the Settings app and go to
General
, then tap
Passcode Lock
, where you can turn
Simple Passcode
off. If you now enable passcodes and choose one that is made up
only
of digits, iOS will provide the numeric keypad when you try to unlock your device.
Of course, this also tells attackers that your code is a number, giving them a leg up on breaking it; however, each additional digit increases the amount of time required for a brute-force attack tenfold, which is certainly
much
better than nothing. For example, going by Apple’s estimates, a six-digit code would require around 22 hours to break, while a nine-digit code could be broken
only
in two and a half years.
This brings me to a crucial point: A passcode isn’t a magic solution that protects your data for all eternity—instead, it
buys you time
before that data falls into the wrong hands. Given enough time and resources, almost any encryption mechanism can be defeated; thus, your goal should be to pick a passcode whose length gives you enough time to neutralize the effects of losing your data.
Buying time
For example, your garden-variety thief will most likely turn on a stolen device as soon as possible to make sure that it works, and will possibly root around for a quick score like your online-banking credentials. In this case, even a nontrivial four-digit passcode will give you enough time to log on to Find My iPhone and remotely wipe the phone’s contents well before the thief can get his or her hands on them.
More-sophisticated criminals, on the other hand, will immediately pop out any SIM card and only turn on the device well out of range of open wireless hotspots, gaining all the time in the world to find their way into your personal data. In this case, your choice of passcode must be commensurate with the amount of time that you want the information on the device to remain inaccessible.
For example, a six-digit numeric passcode will likely give you enough time to reset all your critical passwords, like those you use to access your email accounts and banking websites.
If, on the other hand, you keep confidential data on the device that could remain “hot” for years—legal documents, for example—a long alphanumeric passcode may be necessary to ensure that you’ve at least
tried
to apply a good standard of care in keeping that information secure.
Finding the right balance between convenience and safety is not that hard once you understand how passcodes work; Apple can likely be counted on to fix whatever new vulnerabilities are found in its operating system in a timely manner, but your devices are only going to be as secure as the locking codes you pick.
After all, as
nuclear weapon designers have discovered
, the most sophisticated security mechanism is easily undone by the kind of combination
a character in a science-fiction satire would keep on his luggage
.




