You know you should do more to prevent cyberattacks against your small business, but there’s never enough time.
However, statistics show that without proper precautions, an attack likely could put you out of business: 60% of small businesses will suffer from some type of cyberthreat, and 60% of those businesses will shut down within six months of the breach.
As the number and complexity of cyberattacks rise, all small businesses should make security measures a priority as soon as possible.
Overview: What is an advanced persistent threat (APT)?
An advanced persistent threat employs multiple and continuous hacking techniques to gain access to an organization's IT systems. The ultimate goal is to steal sensitive data such as intellectual property.
Often organized by nation-states or criminal cartels, these persistent attacks are dangerous because they’re difficult to detect and continue their nefarious infiltration long after they initially breach a company’s network. Despite the high-level nature of the threat, many simply begin with fraudulent emails.
“The vast majority of APT compromises begin with email attacks to gain an initial foothold in the victim's environment,” says Matt Stamper, CISO and executive advisor, EVOTEK, and president, ISACA San Diego Chapter. “Most organizations are simply ill-prepared or overmatched by the resources that the threat actors behind APTs can bring to bear.”
As the name suggests, APTs are not quick hits. The attacker takes up residence in the network, sometimes spending weeks or months monitoring communications, collecting customer data, and planting malware throughout the organization, often influencing the network and endpoint device performance.
“APT actors often target specific industries or supply chains, looking for a vector into a larger target such as a tier-one manufacturer, defense contractor, or government agency,” says Mark Sangster, vice president and industry security strategist at eSentire. “But lately, [we’re seeing] more APTs target smaller businesses, either opportunistically to defraud them as a revenue stream or in retaliation for political events such as military aggression or economic trade battles.”
Advanced persistent threat (APT) vs. malware: What's the difference?
Don’t confuse APTs with malware. APT is the threat actor, while malware is one of a variety of tools the actor uses to gain access to your system. When small business owners hear “APT malware,” they assume antimalware software will protect them against an APT attack. Not so.
Typical malware is meant to strike quickly and wreak as much havoc as possible before it’s detected. But APT malware -- often custom-built -- seeks to stealthily infiltrate a network and steal as much data as it can for a longer period of time.
So, while APT hacking may enter a system through malware like Trojans or phishing, the attackers can cover their tracks as they move throughout the system and, undetected, plant malicious software.
“It’s important for businesses to understand that APTs use a wide range of malware, from custom-built toolkits to commodity malware. When people use the term ‘APT malware,’ they’re often referring to the custom, advanced malware -- Stuxnet is a good example,” says Karim Hijazi, CEO of Prevailion, which has tracked many prominent APTs, including Russian, Chinese, and Iranian groups, that also frequently use commodity malware.
“The issue is further complicated by the fact that nation-state cyber activity isn’t as black-and-white as it may seem; there will often be multiple groups involved in these efforts, from the actual APT to criminal groups and contractors who agree to work with the nation-state,” he adds. “This is why an organization that is compromised by commodity malware can then be turned over to an APT operation.”
Types of malware include weapons like ransomware that lock files and disable servers; delivery mechanisms that are good at mimicking legitimate files and are used to deploy other malware without detection; or reconnaissance tools designed to collect information such as user credentials.
As the combination of tools used and the sophistication of the “cover-ups” increase, APT attacks are becoming ever more difficult to identify.
The 9 stages of an advanced persistent threat (APT) attack
To defend against these attacks, it helps to understand each stage so you can develop a strategic, multipronged APT security response that offers layers of protection.
Stage 1: Target selection
According to Patrick Kelley, CTO of Critical Path Security, target selection for APT attacks has become far less specific or intentional. In the past, attackers would do careful reconnaissance to choose a specific company and entry point to gain the desired access.
But in the case of the 2018 attack on the city of Atlanta, for example, the attackers didn’t know that they had breached the city’s network. And in the recent case of a German hospital attack, hackers were targeting a typical corporate environment but missed their mark.
At this early stage, there is not much you can do to protect yourself, other than put in place security measures, keep them up-to-date, and ensure you’re protecting the most vulnerable entry points.
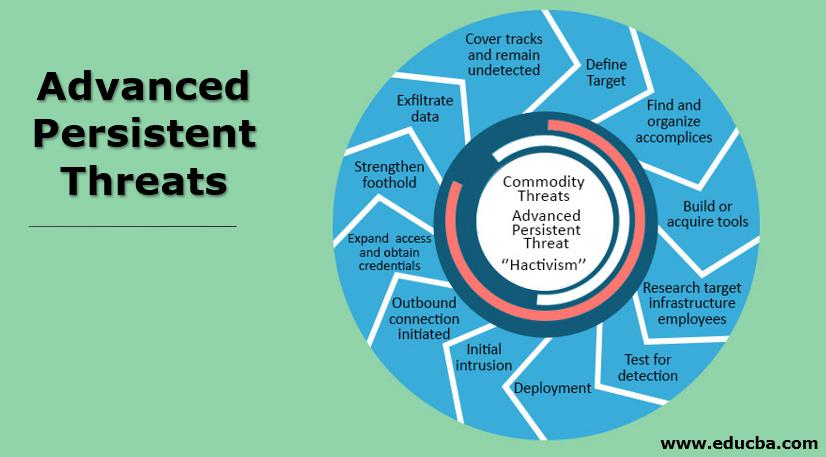
Stage 2: Information gathering
Once a target has been determined, hackers collect as much data as possible in advance of the attack, essentially “casing the joint” to understand the comings and goings of those who access your network. They often collect breached credentials or vendor data they can later use to gain entry to your network through trusted channels.
Password managers and two-factor/multi-factor authentication are your best defense against hackers at this stage.
Stage 3: Point of entry
After choosing the target and planning/building the attack tool, attackers “deliver” it to the target. Typically, a point of entry is the weakest point of the network, and humans -- and their often careless endpoint security measures -- may be that weak point.
“With over a billion leaked credentials per year, humans are the point of entry,” says Kelley. “Using leaked credentials can provide access to the VPN, remote desktop services, and cloud accounts. The value is in the data, not the hardware.”
Your best defense? Explore the best endpoint security software, then use password managers and two-factor authentication.
Stage 4: Escalate privileges
This is the stage where APTs distinguish themselves from commodity malware. Rather than strike, damage, and leave as quickly as possible, the attackers expand the threat to cover as much of the network as possible.
This is far easier than it was in the past. With today’s work-from-home scenarios, it’s nearly impossible to keep every vulnerability patched, yet more and more remote workers are logging into the network with little or no endpoint security protecting their home laptops. Finding an unpatched system or documentation with stored credentials is incredibly easy for hackers, who then gain access to any system on the network.
Perhaps the simplest thing you can do is keep up with software patches, which vendors issue regularly.
“Patch everything. Have a posture that includes defense-in-depth,” says Kelley. “If a system is compromised, ensure that proper firewalls or VLANing is taking place to reduce the impact of the breached system.”
Stage 5: Command and control communication
Once your system is infected, it signals the attacker’s server for further instructions, providing the threat actor complete control of your network. This happens because very few networks block outbound traffic. A common method for hackers is using Twitter Direct Messaging to send the signal and communicate with the server, but if that connection can’t be established, they’ll find another method.
At this point, you would need visibility into incoming and outgoing network traffic, proper outbound firewall rules, and behavioral detection to defend against the attack; but there’s still a good chance you won’t be able to detect the breach.
Stage 6: Lateral movement
At this stage, the attacker collects additional user credentials and continues to expand control over your servers and workstations. They’ll plant malware such as ransomware across the network and in backups to make quick recovery extremely difficult.
According to Kelley, the threat actors typically look for multifunction copiers or VoIP phones to move their persistent tunnels because those types of devices are rarely monitored and typically maintained by a third-party vendor. However, both have full operating systems that permit the attackers to conduct nearly all functions that a fully monitored server or workstation provides.
Visibility and behavioral detections are critical at this stage. Virtual local area networks (VLANs) perform better from a security standpoint because they limit lateral movement, as they separate broadcast links from the data layer of your network. However, Kelley notes, as the attackers move through the stages, it becomes much harder to stop the attack.
Stage 7: Asset discovery and persistence
At this point, the attacker has discovered and accessed most of your assets. This typically takes less than 24 hours. How long the attackers will persist depends on how many attack points they need, including external entry points, which they use in case one of the other points is detected and blocked.
Again, the defense against this stage of the attack includes visibility into network activity, proper outbound firewall rules, and behavioral detection.
Stage 8: Exfiltration
Finally, the attackers transfer data from your network to their servers. This can be accomplished in a number of ways, including file transfer protocols (FTP), email, or ICMP and DNS queries, which are simply requests from the attacker’s computer asking for information from your server. Often, attackers move data very slowly so they can avoid detection and remain in your system longer.
Visibility, proper outbound firewall rules, and behavioral detections remain critical to defense at this stage. Additionally, Kelley recommends restricting access to data in a need-to-know system: “If a breached account can only access a small subset of data, there is less information that can be exfiltrated.”
Stage 9: Withdrawal
Ultimately, the hacker carefully withdraws from the system and covers their tracks to reduce detection. However, they may leave “back doors” to infiltrate the organization in the future. In some cases, they may simultaneously detonate ransomware to shut down operations, then demand a six-figure payment to return systems to operational status.
“Most attacks are active for an average of 240 days before an organization figures it out,” says Kelley. “At this point your best defense is good legal counsel.”
FAQs
While some of these tools may be a bit more complex to deploy, small businesses shouldn’t forget to use the simple tactics everyone should use, but often don’t: traffic monitoring, application and domain whitelisting, controlling access to sensitive data, encrypting remote connections, and filtering incoming emails.
Endpoint detection and response (EDR) tools are deployed on endpoints (laptops and workstations) as well as on servers (whether on-premise or in the cloud). They bring important security protections and the ability to detect adversaries “living off the land,” using common tools like PowerShell and techniques that include process and DLL injections.
“Many forms of malware don't necessarily result in a signature that can be used by antimalware applications but rather anomalous behavior within an environment that could offer warnings of adversarial behavior,” says Stamper.
“Modern malware frequently runs in memory and has been designed to ‘hide in the open’ and look like legitimate activity using normal processes within the operating system. This is the primary reason why EDR tools require machine learning and cloud backends to sift through millions of events to determine which is the bad ‘needle’ in a haystack full of needles.”
Smaller companies often don’t believe they are APT targets because they can’t imagine that a nation-state would know or care that they exist. Because they don’t believe they’re at risk, these firms don’t protect themselves and are easy prey for APTs.
“I show clients trend data that demonstrates a growing presence of APTs and nation-states in smaller businesses,” says Sangster. “Our security operations centers see a spike in attacks following tectonic events like a missile exchange in the Middle East and trade disputes with China. We’ve seen a state Supreme Court under attack, a telecommunications vendor
infiltrated to establish backdoors in their technology, and a law firm targeted in retaliation for their representation of a client deemed a dissident by their home nation.”
Facing the threat
While small business owners may downplay the risk an advanced persistent threat poses, these incidents are increasing in frequency, and the results can be devastating.
While antivirus and antimalware software are necessary and effective for some issues, most small businesses could benefit from consulting a cybersecurity professional to evaluate their system, identify vulnerabilities, and recommend best practices to keep sensitive data secure from malicious actors.
Depending on the size of your business, it may be time to set up an in-house security operations center (SOC) to provide ongoing threat monitoring, patching, and incident response.
APTs are proof that it’s never too soon to protect your most valuable assets.




