Image source: Getty Images
Cyberattacks are growing in sophistication, requiring new solutions to protect your IT systems. Endpoint detection and response (EDR) is a modern approach to cybersecurity. Learn how EDR works.Small businesses are increasingly targeted by cybercriminals. Last year, 66% of small businesses experienced a cyberattack. Increasingly, companies turn to endpoint security software to protect information technology (IT) networks.
Yet, a challenge remains. Cybercriminals employ so many tactics to circumvent your defenses, it’s not feasible to stop all attacks every time.
Today’s advanced security technology acknowledges this reality and includes the ability to address threats that sneak through your defenses. One of the most popular and effective approaches is endpoint detection and response (EDR).
What is endpoint detection and response (EDR)?
Endpoint detection and response is an increasingly popular security measure for one key reason: visibility. This is the essential element required to stop a cyberattack infecting your systems.
When an attack penetrates your defenses, alarm bells don’t go off. In fact, you’re not going to know an attack is happening for some time.
It takes businesses an average of 197 days, more than six months, to detect and stop an attack that slipped through endpoint security. This type of cyberattack, called an advanced persistent threat (APT), is complex and designed to inhabit your network undetected for lengthy periods of time.
Endpoint detection and response finds these elusive attacks. EDR involves continuous monitoring of your IT systems combined with automated data analysis to identify suspicious activity on your endpoints (the computing devices used on your IT network, including laptops, mobile phones, and servers).
EDR comprises detection, investigation, and response capabilities. Image source: Author
With EDR, your endpoints’ typical behavior becomes well understood. When that behavior changes due to an attack, you’re alerted and can act to contain the threat.
3 important elements of effective endpoint detection and response (EDR) security
These components are necessary for EDR security to succeed. These elements create the visibility required to identify and act on a security breach.
1. Data collection and storage
Every EDR solution relies on data as the foundational element to create the visibility to catch attacks. Two components comprise the data piece.
2. Analytics and forensic capabilities
To identify potential attacks, EDR systems must sift through the collected endpoint data to flag anomalies. This investigation requires real-time analytics performed by automation and forensic tools employed by IT security professionals, such as threat hunters or a security operations center (SOC).
3. Fast response
Once analysis confirms a threat, your EDR must perform swift action. Quick response to security incidents helps you minimize or prevent damage such as stolen financial or customer data.
The incident response can range from sending out automated alerts and automatically logging out the endpoint user to shutting down network access and isolating the endpoint before an infection can spread. Any EDR technology you’re considering should support several response options you can adjust based on your needs.
How endpoint detection and response (EDR) works
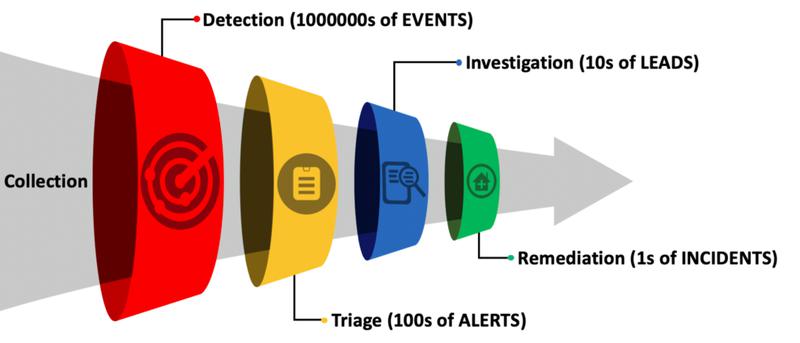
Successful EDR security involves detection, triage, investigation, and remediation capabilities. These represent stages in filtering through endpoint data to target the cyber threat.
1. Detection
The EDR security process begins with threat detection. For an EDR’s automated systems to find threats, you install a software agent onto your endpoints to perform data collection.
The agent constantly monitors the endpoint and collects telemetry data, sending it to a central database where machine learning algorithms analyze the data for anomalies. Sudden changes in endpoint processes or user behaviors from normal conduct get flagged for further investigation.
Examples of suspicious activities include attempting to log in to an endpoint from a remote location, downloading certain types of software files, or disabling firewalls. EDR combines these signs of irregular behavior with the chain of events before and after to create a map of the executed processes.
With this broader context, combined with threat intelligence, EDR systems can evaluate the billions of events across your network to narrow down the activity indicative of a cyberattack.
2. Triage
EDR platforms notify IT staff of suspicious activity. They send alerts and provide dashboards and reports summarizing the results of algorithmic findings.
This is when the triage occurs. The IT team must eliminate the false positives. They also classify the alerts as known malicious activity, which immediately triggers the remediation stage, or unknowns for investigation.
The triage phase is the most challenging for IT teams. They are often overwhelmed with alerts, and the team can miss activity requiring deeper investigation.
To prevent this, IT teams must routinely review EDR detection criteria to address the following.
3. Investigation
The triage phase pares down the universe of detected anomalies to the unknowns, called leads. From there, it’s time to dig into the leads to confirm benign or malicious activity.
The IT team examines each lead using threat hunting techniques to collect additional context. This context enables better understanding of the activity and why it’s happening. For instance, an unfamiliar computer process executed on an endpoint could signify an attack or simply that an employee downloaded new software.
The key to the investigation stage is speed. You want to determine if unknown activity is malicious quickly to contain any damage.
Today’s cyberattacks employ lateral movement, a tactic that allows infections to move from one endpoint to others, rapidly infecting large parts of your network. A good EDR system accelerates the investigation phase, leading to faster response and remediation to contain lateral movement.
4. Remediation
Confirmed threats require a response so EDR platforms can automatically act.
Responses include tactics such as stopping any computer processes running on the infected endpoint and isolating the endpoint from the rest of your network. Some EDR solutions can automatically salvage files and data stored on the endpoint while removing the infection.
Part of remediation efforts involves your IT team determining the extent of the damage. Was customer data stolen? What network vulnerabilities need addressing?
Understanding the cybercriminal’s target and how the attack occurred allows you to take the proper actions. It also enables your team to collect specific knowledge to strengthen your network security.
The EDR process is like a funnel sifting through data to zoom in on threats. Image source: Author
FAQs
A final word about EDR
It’s easy to view endpoint detection and response implementation as a low priority. You’d rather ensure threats can’t get past your security in the first place. But a single employee tricked into clicking on an emailed file can trigger an attack that bypasses your defenses.
EDR puts the power back into your hands. Rather than reactively cleaning up after a cyberattack and hoping sensitive information wasn’t stolen, use EDR to proactively find and stop attacks.
The proliferation of endpoints, such as tablets and smartwatches, combined with the increasing sophistication of cyberattacks makes EDR a key component of every organization’s IT security.




